Using FatRat To Create Reverse HTTPS BackDoor
This lap was extremely tricky. I had to first go to FATRAT github page - downlaod the software to my KALI linux and install it. This information is provided for educational and defensive purposes to help cybersecurity professionals, students, and system administrators...
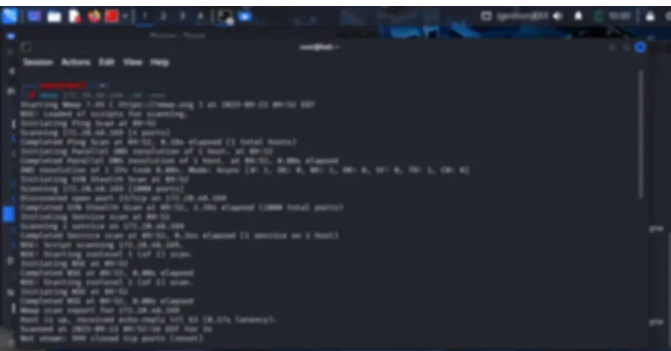
My Hackviser Warmup Journey: 4 Labs That Kickstarted My Penetration Testing Skills
INTRODUCTION When you start your penetration testing journery can be extremely overwhelming. For me, I have done course on Udemy and other platfrom (hackthebox, Josh Matador Cyber Range etc)To build my skills. Anyhow I began working through the Hackviser Warmup...
SpiderFoot: A Comprehensive Guide to Installation and Usage
SpiderFoot is an open source intelligence (OSINT) automation tool. It integrates with just about every data source available and utilises a range of methods for data analysis, making that data easy to navigate. SpiderFoot has an embedded web-server for providing...
Secure Your Network with Reliable Penetration Testing Services
Welcome to a smart way to protect your business from online dangers. Use professional methods that copy real hacker attacks. This helps us find weak spots in your security before bad actors can. Today, every company in Jamaica faces more risk from clever cyber...
Cybersecurity Best Practices for a Safer Online Experience
Our world is more connected than ever. From Kingston to Montego Bay, businesses and individuals rely on digital tools daily. This digital landscape brings incredible opportunities but also significant risks. Understanding security fundamentals is no longer...
Incident Response Strategies: Prepare Your Business for Emergencies
Welcome to your essential guide on protecting your Jamaican business. In today's digital world, cyber threats are constantly changing. Preparing for emergencies is no longer optional. It is a critical part of running a successful company.Cyberattacks and data breaches...
Comprehensive Guide to Compliance Frameworks
Navigating today's complex business rules can feel overwhelming. For companies in Jamaica and around the world, having a clear system to manage legal obligations is essential. These structured approaches provide much-needed guidance in a sea of regulations.The...
Mastering Malware Protection: Essential Techniques to Stay Safe
Our digital world offers incredible opportunities, but it also comes with serious risks. Unwanted software, created by malicious actors, is a constant danger. These threats can disrupt your systems, steal sensitive data, and cause major financial harm.According to...
Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
Mastering the CIA Triad and IAAA for Stronger Cybersecurity
Welcome to your guide on building a powerful digital defense. We will explore two core frameworks that form the bedrock of modern cybersecurity. Understanding these concepts is the first step toward protecting what matters most.This guide is designed for everyone....
About This Project
I’m a cybersecurity student documenting my labs, so I can track my progress and show employers what I can do. Each writeup contains objectives, environment, step-by-step methodology, findings, and recommended remediation. All testing is doe in isolated labs using intentionally vulnerable targets.
- Environment: VirtualBox / Host-Only networks, kali linux
- Tools: Nmap, Wireshark, Burp Suite (community), John/Hashcat
- Focus: Pratical labs that teach defensive and offensive thinking
Interested in my progress or want to offer feedback? Reach out.