INTRODUCTION
When you start your penetration testing journery can be extremely overwhelming. For me, I have done course on Udemy and other platfrom (hackthebox, Josh Matador Cyber Range etc)To build my skills. Anyhow I began working through the Hackviser Warmup Machines, a set of beginner-friendly labs designed to teach real-world techniques in a safe environment.
In this post, I share my experience solving four machines: Arrow, File Hunter, Secure Command, and Query Gate and the key lessons each one taught me.
ARROW
Objective: Gain initial access and escalate privileges.
Approach:
i. Performed an Nmap scan to identify open ports and running services.
ii. Discovered an exposed Telnet service and connected to it for entry.
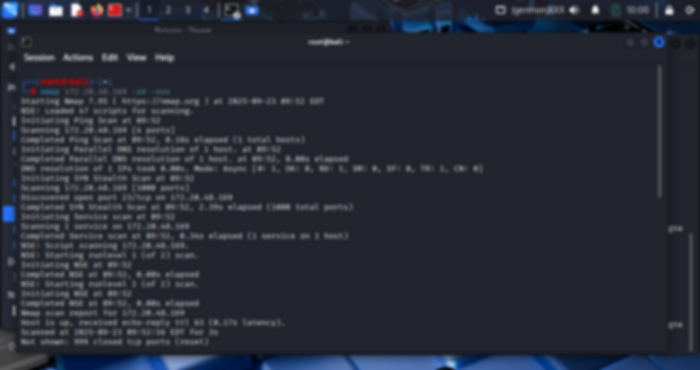
I began with an Nmap scan to discover open ports and running services on the target host:
nmap <target_ip> -sV
- -sV: Enables service/version detection, allowing Nmap to probe each open port and identify the exact service and version running.
This scan revealed the services and their versions, which guided the next steps of enumeration and exploitation.
Exploitation Phase
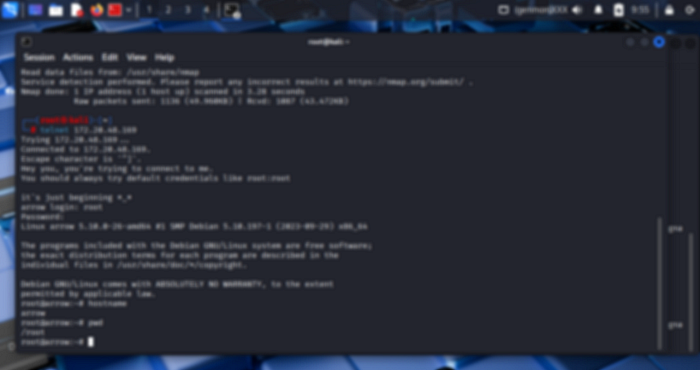
The Telnet service was identified as open during the scan, which allowed a login using default credentials.
This provided direct access to the target host.
Commands used:
i. telnet <target_ip>
Connect to the target over the Telnet service.
Logged in with the service’s default username and password.
ii. pwd
Display the current working directory.
iii. hostname
Reveal the system’s hostname to capture the flag.
- Key Takeaway: Enumeration is everything. Even a “simple” service like Telnet can become a critical attack vector if misconfigured.
